Syrian Electronic Army: Disruptive Attacks and Hyped Targets
Crossposted from the InfoWar Monitor.
Introduction
In The Emergence of Open and Organized Pro-Government Cyber Attacks in the Middle East: The Case of the Syrian Electronic Army, the Information Warfare Monitor’s Helmi Noman started documenting the activities of the Syrian Electronic Army (SEA), which appears to be a case of an open and organized pro-government computer attack group that is actively targeting political opposition and Western websites. That report documented how Syria has become the first Arab country to have a public Internet Army hosted on its national networks to openly launch cyber attacks on its enemies.
In this report, the IWM continues to examine the SEA’s activities, their online targets, and the impact of their attacks.
Overview
On June 20, 2011, the president of Syria, Bashar al-Assad, stated his appreciation for the SEA’s efforts and described it as a real army in virtual reality in a televised speech to the nation. The SEA stated on its website that it was honored by the mention in the Presidential speech but reiterated that it is not affiliated with any government entity. Although we have no concrete evidence linking the SEA to the Syrian regime, the President’s statement, and the fact that the group is able to operate with impunity over Syrian networks, shows at least tacit support for their activities.
The SEA continues to claim responsibility for defacing or otherwise compromising scores of websites that it contends spread news hostile to the Syrian regime. After a 4-day countdown meant to build anticipation, the SEA announced the defacement of over 130 websites and has continued to release the URLs of more defaced pages every few days. Although we verified that most of the websites were indeed defaced, the vast majority of the affected pages were online businesses and blogs with no apparent political content.
The SEA has intensified its efforts to target Israeli websites based on claims that some of these sites contain content that is antagonistic to Syria and Palestine, and also supposedly as revenge on Facebook for continually disabling the SEA’s pages. The SEA did not provide details explaining why they perceive Facebook to be related to Israel. Although one of the targeted sites was associated with an Israeli member of Knesset, the majority had no political content. Many of these defaced sites share IP addresses, indicating that far fewer compromises actually occurred than what appears upon first glance.
The SEA has continued with the Facebook comment spamming campaigns we described in our last report. They also recently linked to a video that documents defacement of five Facebook pages of Syrian political opposition groups, changing the profile picture of each to the SEA logo.
The group and its affiliates continue to disseminate denial of service (DoS) software designed to target media organization websites. We have acquired and analyzed the software and found that it is designed to perform denial of service on the websites of Al Jazeera, BBC News, Syrian satellite broadcaster Orient TV, and Dubai-based al-Arabia TV. A group calling itself the “Syrian Hackers School” has a Facebook page that promotes the DoS tool, recruits members, and provides links to resources for learning how to compromise vulnerable websites.
The SEA has also started to infiltrate a number of Syrian political opposition Facebook pages and replace the original content with SEA logos and post pro-regime messages.
Syrian Electronic Army Attacks on Hyped Targets
Following the SEA’s announcement of mass defacements we verified that most of the websites were indeed defaced at the time, some by the handle “ArabAttack”, whose name has also appeared on previous SEA defacements, and others by “The Shadow”, whom we had not seen before. Other handles seen previously, such as “The Pr0”, “Saqer Syria”, “Sy Team” and “al3rab” did not appear in any of the new defacements (See Figure 1).
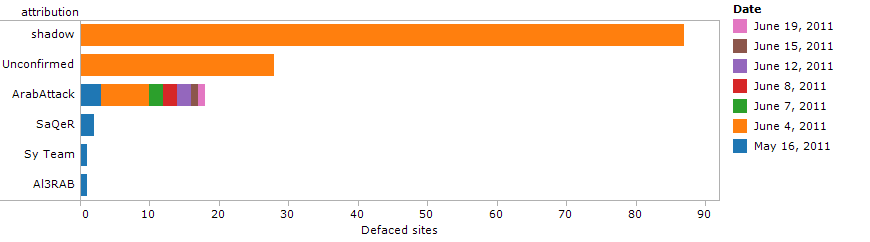
Figure 1: Defaced sites by date and attacker.
The 122 domains the SEA claimed responsibility for attacking on June 4th resolve to only 15 unique IP addresses, which indicates that the high volume of sites was likely due to a few mass defacements achieved by exploiting a single vulnerability on a shared web server (See Figure 2).
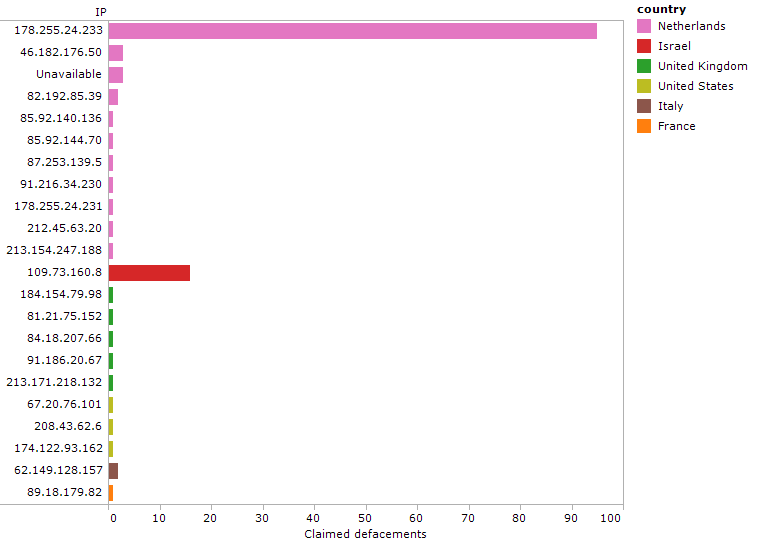
Figure 2: Claimed defacements by IP and country, May 16 – June 19, 2011.
The first URL reported to be defaced by the SEA, http://o3touch.com, had an HTML tag inserted into it causing a redirect to http://justnulled.com/i/ind.htm, with a defacement image from ArabAttack claiming responsibility under the banner of the SEA. The SEA’s announcement stated that the compromise was committed as a protest against US interference in Syrian domestic affairs, and also mentions Microsoft. However, the site in question is actually an Israel-based company that sells software for Windows Mobile phones. Both o3touch.com and justnulled.com resolve to the same IP address, suggesting that both sites may have been compromised through a single breach. On the other hand, we were also able to confirm that the redirect tag had been injected into a database table, whereas the target page would likely needed to have been uploaded directly to the site, indicating a possible second vulnerability.
The majority of the defaced sites were announced in the SEA’s three subsequent posts. Once again, these were almost all online business websites, and most of them had the Internet country code top-level domain (ccTLD) for the Netherlands (.nl). These defacements were claimed by The Shadow, who, like ArabAttack, explicitly mentioned the Syrian Electronic Army.
We verified that most of these websites were indeed defaced at the time, and also found that 95 of the sites had been previously defaced on May 13, 2011 by an entity calling itself Reza_0o0, associated with “Iranian Hackers.” (We cannot confirm if this entity is a single person or a group of attackers). Most of these websites still carried Reza_0o0’s defacement in addition to the defacement text placed by the SEA. Unlike the SEA, which defaced the front page of each site, Reza_0o0 “tagged” the sites in a more subtle way, leaving a file named r.htm accessible at the root of each site. For example, the site at http://aaddejong.nl by default looked like Figure 3 (below), but Reza_0o0’s defacement text can still be accessed at http://aaddejong.nl/r.htm (See Figure 4).
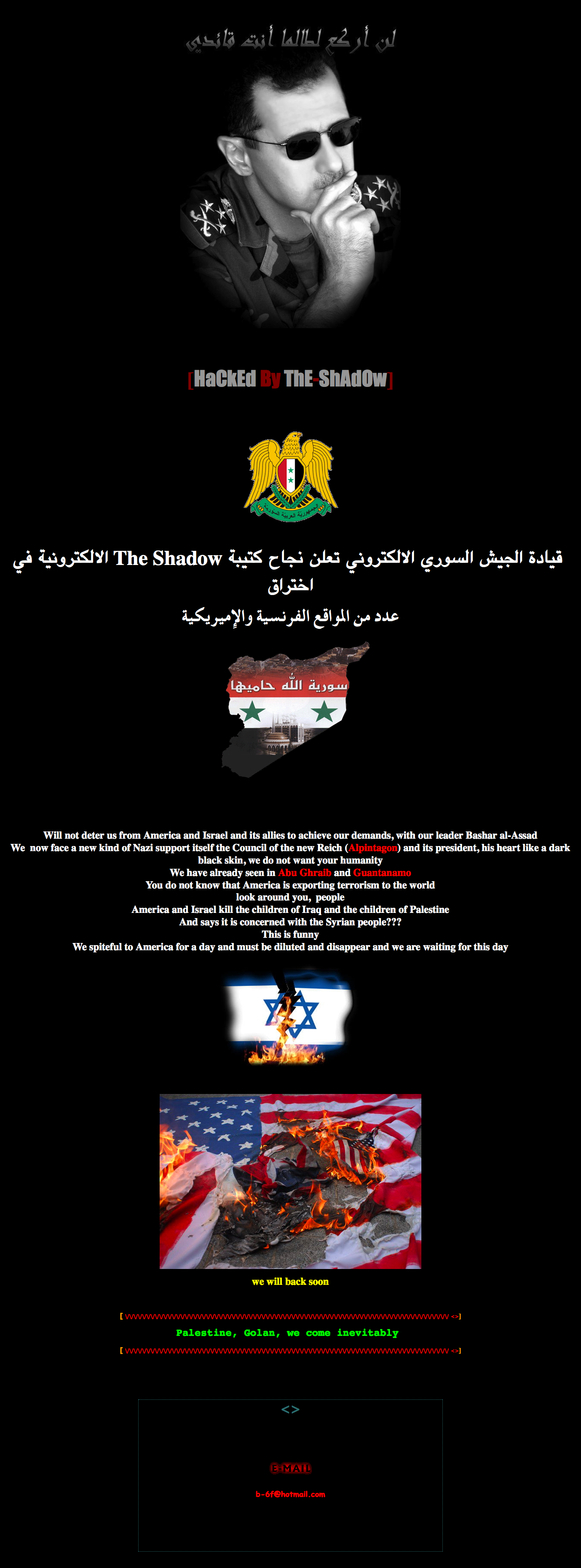
Figure 3: IWM mirror of http://aaddejong.nl as defaced by the Syrian Electronic Army.

Figure 4: Screenshot of http://aaddejong.nl/r.htm as defaced by Reza_0o0.
Reza_0o0 reported and uploaded screenshots of the affected websites to zone-h.org, an online archive of defaced websites, on May 13, 2011. As of June 25, 2011 Reza_0o0 had reported a total of 945 defaced websites, of which 773 were mass defacements, since December 11, 2010.
The fact that these pages were defaced by both an Iranian entity and the SEA may indicate some kind of collaboration between them. We will explore such connections in our ongoing research efforts. However, it is more likely that these were soft targets, chosen for the ease of breaching them. Both the SEA and Reza_0o0 left traces to external websites via tag references – The Shadow left a link to the Arabic underground hacking forum http://www.aljyyosh.com, and Reza_0o0 linked to a now-missing image hosted on a server which contains an open directory of web hacking tools.
Defacement Attacks on Israeli Websites
In another of the June 4 SEA announcements the group claimed responsibility for compromising 6 websites that it described as top Israeli websites that spread poisonous [information] and instigate killing of our Palestinian brothers.
We confirmed that the websites were defaced, and found that none of the 6 targeted sites were news websites or carried content related to Syria or Palestine. The websites included an online shop, a plastic products company, and personal websites. The defacement text left on those websites read:
Hacked by Arab Attack under the Brigade of the Syrian Electronic Army to commemorate the Naksa Day.” (See Figure 5).
Naksa Day (day of setback) is the annual day of commemoration (June 5) for the Palestinian people of the displacement that followed Israel’s victory in the 1967 Six-Day War.
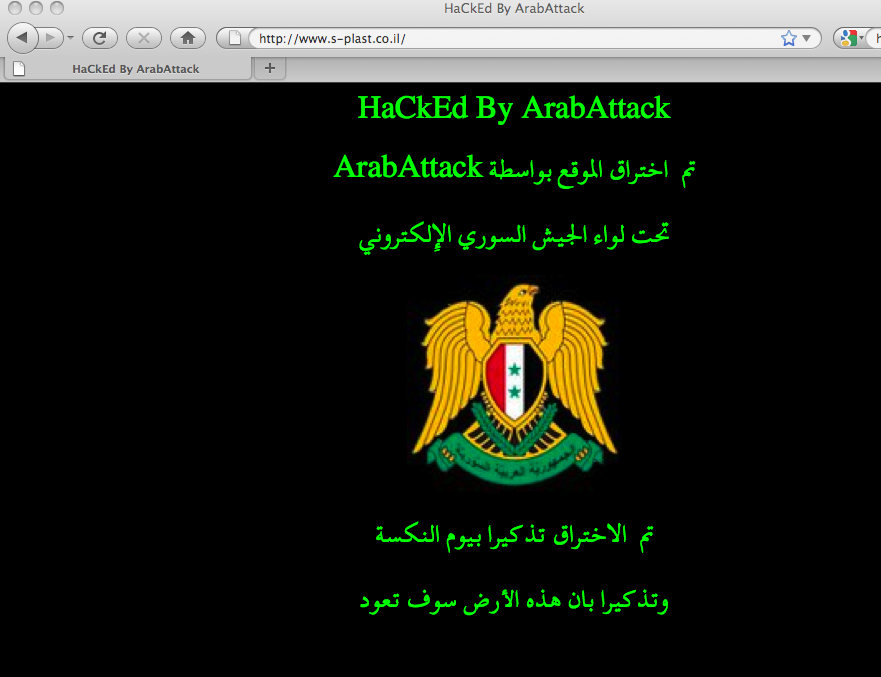
Figure 5: Screenshot of an Israeli plastic products company defaced by the Syrian Electronic Army.
On June 7, 2011, the SEA announced it compromised more Israeli websites; the website of the Israeli Member of Knesset Arieh Eldad (http://www.arieheldad.com) and a tourism site (http://soloisraele.com). The SEA said it deleted all content on the sites and claimed to target these Israeli websites “as a revenge from Facebook which keeps removing our pages” but did not explain what connection there was between Facebook and Israel. We verified that the website of the Member of Knesset was defaced with the following message:
Hacked by Arab Attack under the Brigade of the Syrian Electronic Army to commemorate the Naksa Day.” (See Figure 6).
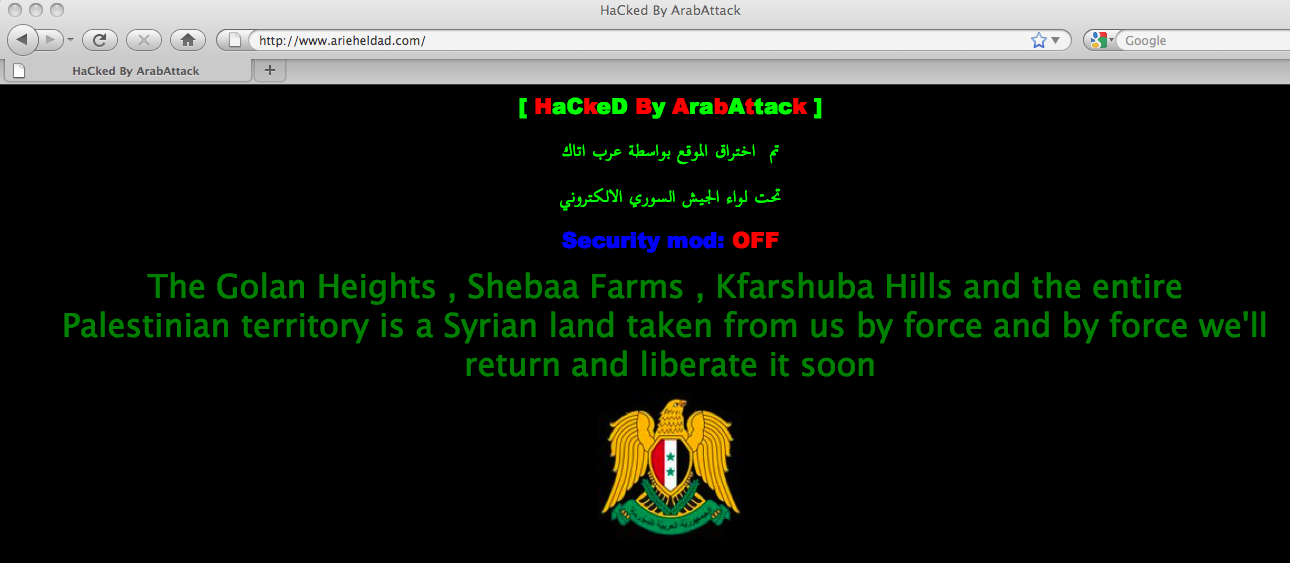
Figure 6: Screenshot of defaced website of Israeli Member of Knesset Arieh Eldad.
On June 12, 2011, the SEA claimed responsibility for compromising two more Israeli websites and said these targets were chosen as part of an operation to cleanse up the web from Israeli websites that promote hatred towards the Palestinian people. We confirmed that the two websites were defaced and found that neither had political content. One of the sites is an online directory of lawyers in Israel (http://www.lawyerfinder.co.il), and the other is a blog about personal computers (http://www.pc-blog.co.il). The defacement text was the same as in Figure 6.
On June 15, 2011, the SEA defaced the website of the Center for Small Business in Israel (http://ismbc.co.il), and on June 19, 2011 the website of the Israel Chemical Society (http://www.chemistry.org.il).
We found that all of the targeted Israeli domains resolve to the same IP address: 109.73.160.8. This is the same address for two of the domains claimed by the SEA on June 4th (o3touch.com and justnulled.com), and at least one of the newer sites, soloisraele.com, was compromised via the same HTML redirect injection used against o3touch.com. However, other websites were defaced by a different method, possibly through the same vulnerability that gave the attacker access to justnulled.com. By using a reverse IP lookup we were also able to find two more defaced sites that the SEA did not announce on their site. In contrast with the strategy used for the Dutch domains on June 4, where they announced a large number of defacements at once, the SEA opted to deface and publicize these Israeli sites a few at a time, possibly to maintain the hype surrounding their activities without having to find new vulnerable targets (See Figure 7).

Figure 7: IP addresses of confirmed defaced websites.
Defacements by Affiliated groups
In the last of their June 4 announcements, the SEA announced that other groups of Arab hackers targeted 10 websites it described as American and British news websites as a contribution to the SEA. We verified that the websites were defaced and found that none appeared to be news websites. Rather, they were websites of private companies, blogs and forums based mostly in Brazil, and one in Thailand (listed below).
The defacement text on these websites read:
Hacked by
Yemen Hackers
Muslim Hackers
Arab Hackers
For Free Palestine
The defacement page displayed the flags of Palestine, Syria, Egypt, Yemen, Lebanon, and a banner that read “Third Palestinian Intifada.” (See Figure 8 and Figure 9).
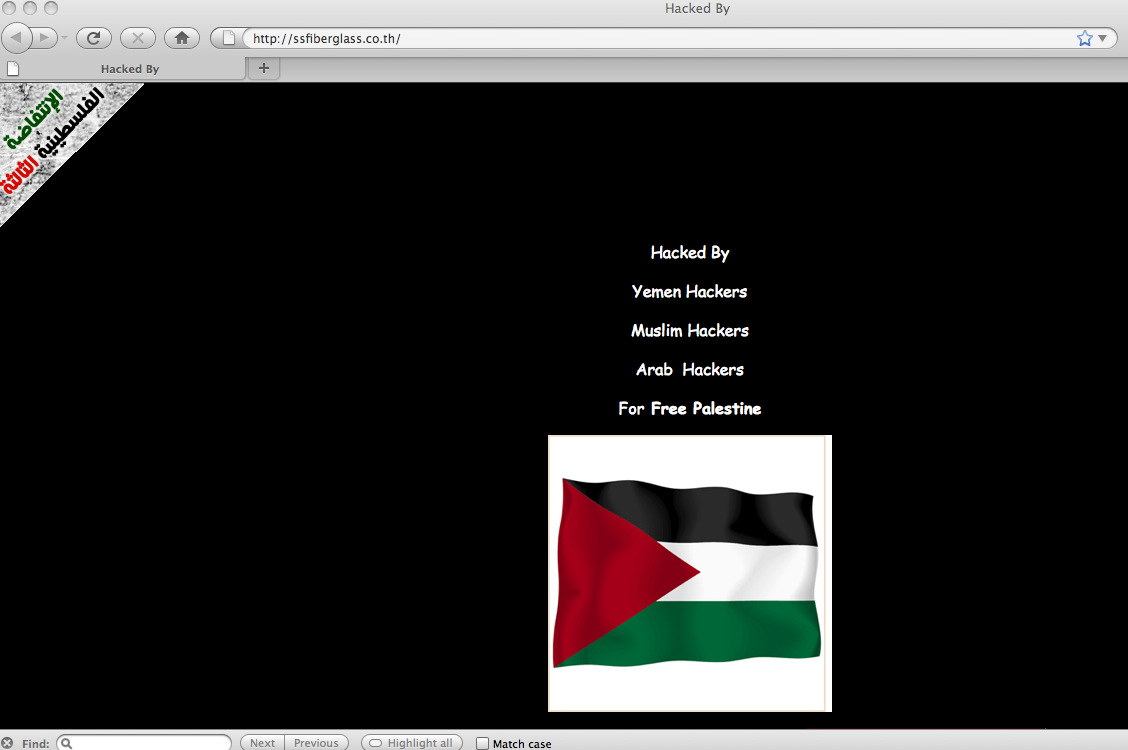
Figure 8: Screenshot of a defaced Thai website.
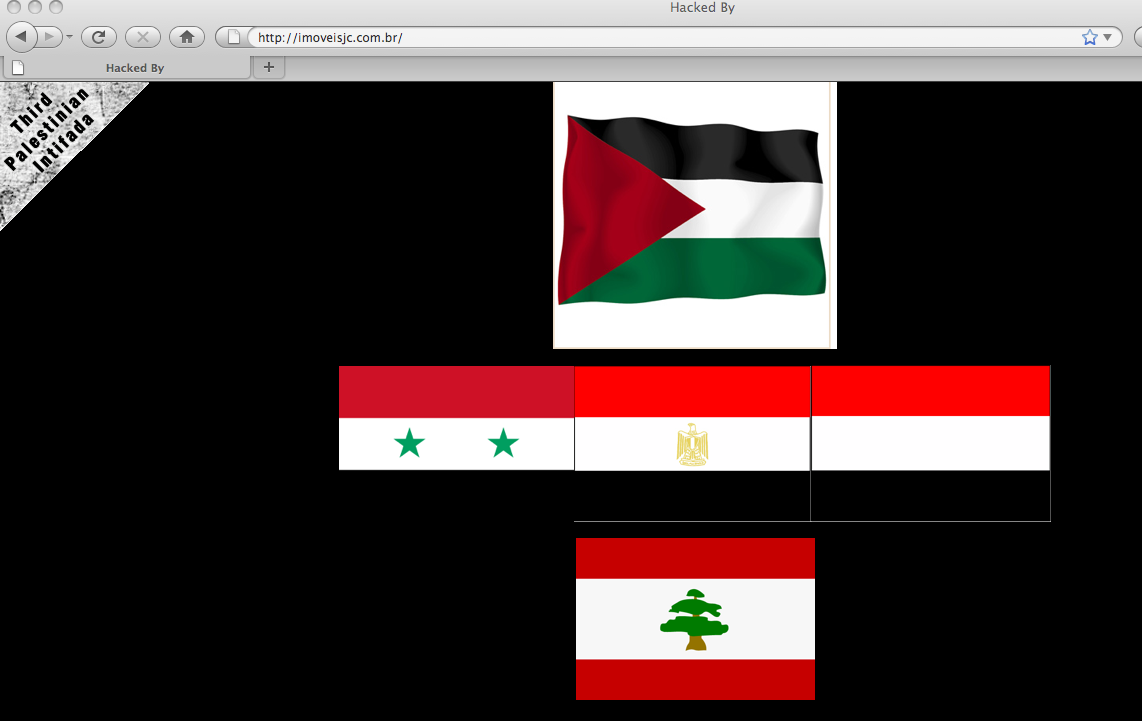
Figure 9: Screenshot of a defaced Brazilian website.
Denial of Service and the Syrian Hackers School
The Syrian Electronic Army and other pro-regime groups have started what constitutes a virtual academy to recruit and educate sympathizers on how to use Denial of Service (DoS) software and computer exploitation and infiltration techniques. Earlier this month, the group posted an announcement on Facebook seeking recruits who speak different languages, and provided an email address for interested individuals to send details and time of availability (See Figure 10).

Figure 10: Screenshot of the SEA Facebook announcement.
We acquired the DoS software “Bunder Fucker 1.0” from the links available on the SEA’s Facebook pages. The software’s interface indicates it is developed by a person known as Alex Izeld. The software is named after the Bandar bin Sultan, a prince of the Saudi royal family who had served as the Kingdom’s ambassador to the USA. The interface displays an image of Bandar bin Sultan beside an image of a donkey (an insulting combination in Arabic culture) as a logo (See Figure 11). Syrian local media have accused the Saudi prince of conspiring to destroy the country.
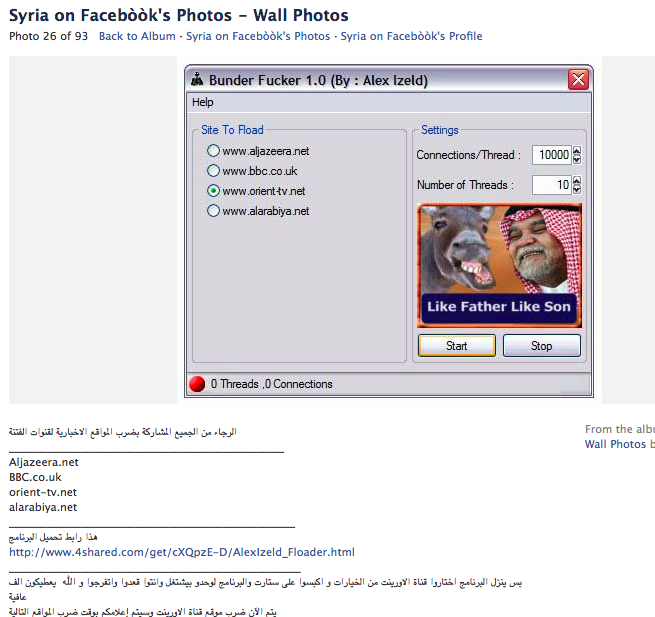
Figure 11: Screenshot of Facebook that distributes links to download the DoS software.
The software targets four news websites: Al Jazeera (www.aljazeera.net), BBC News ( www.bbc.co.uk), Syrian satellite broadcaster Orient TV, (www.orient-tv.net), and Dubai-based al-Arabia TV (www.alarabiya.net). The group claims the four websites were targeted because they spread biased and hostile information about the protests in Syria.
In an ironic twist, pro-revolution hackers have re-purposed the same software to target Syrian government and pro-regime websites. The alternative version was made available through opposition websites and a blog containing pro-revolution content and information on computer exploitation and infiltration. The targeted sites were the website of government General Organization of Radio and TV (rtv.gov.sy), Addounia TV station (addounia.tv), and Syrian news websites syriarose.com and syria-news.com (See Figure 12).
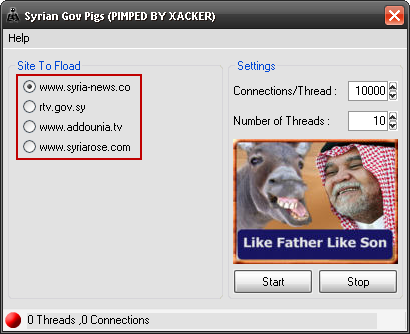
Figure 12: Version of the DoS tool modified by pro-revolution hackers.
Our analysis of the software reveals that it is a simple denial of service tool, meant to be used by many people at once as part of a manual distributed DoS attack. It is packed (compressed and obfuscated) using PECompact, which is relatively easy to unpack. The ease of unpacking the program may explain why it was re-purposed against pro-Syrian sites; once unpacked, only minor changes to text fields are necessary to turn it against its creator. These kinds of alterations are exactly what happened with the “Syrian Gov Pigs (PIMPED BY XACKER)” version of the tool: only text fields have been changed, even the original pro-Syrian images remain.
The program allows users to select one of four targets, set the number of parallel execution threads and how many connections to make per thread, and then connects to that website repeatedly over TCP. The TCP connections are established and closed normally, which is unlike other DDoS tools that attempt to leave connections in half-open states. This full-connection attack is very simple and “loud”, and relies entirely on the number of simultaneous connections at any given time to overwhelm the target. While the attack is very basic and can be implemented very easily, it can still be effective when used by many people at the same time.
In addition, the SEA and its supportive groups direct sympathizers to various related resources including websites that have been already compromised, and encourages them to practice their skills on the compromised websites. One of the Facebook pages that disseminates resources for computer exploitation and infiltration techniques belongs to a group calling themselves the Syrian Hackers School. In the screenshot below (See Figure 13), the page owner for the Syrian Hackers School posts a list of compromised websites and explains that the exploited shell is available for users to manipulate.
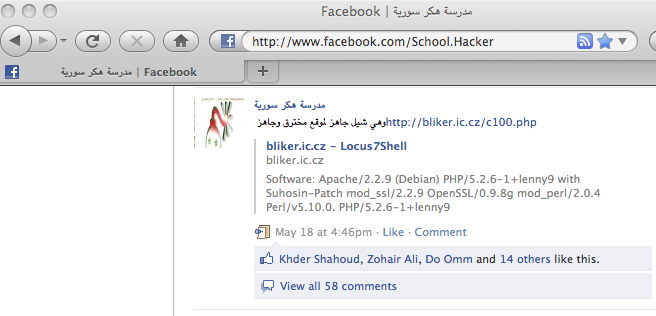
Figure 13: Screenshot of Facebook page School Hacker publicizing a compromised website.
We examined the website and found it had indeed been compromised and that it was made available for vulnerable to further exploitation (See Figure 14. The technique used is known as SQL database injection, which exploits a security vulnerability occurring in the database layer of an application. This technique seems to be commonly used by the SEA and it is demonstrated in YouTube clips that document SEA attacks. Many of these video clips are posted on the group’s YouTube channel.
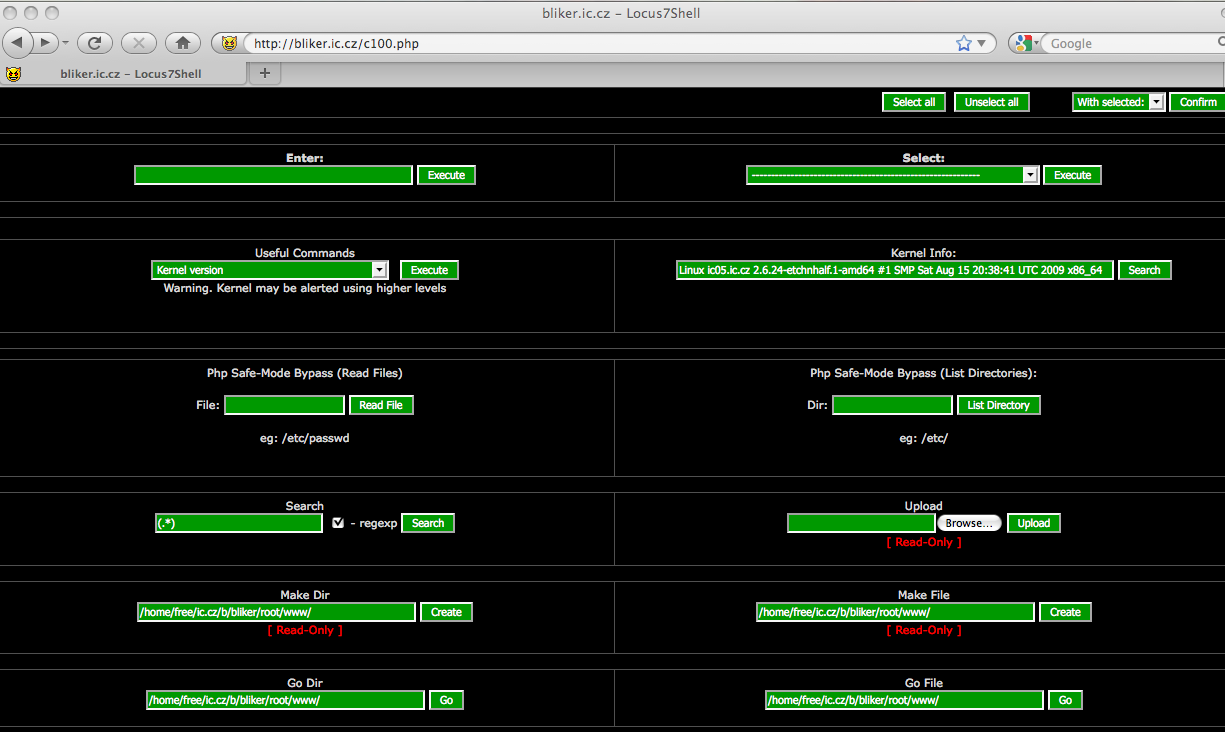
Figure 14: Screenshot of a compromised website publicized by the Syrian Hacker School Facebook page.
Compromising Opposition Facebook Pages
Starting on June 20, the SEA began to compromise and infiltrate opposition Facebook pages and replace their anti-regime logos with that of the SEA (see here and here). Through access to these pages the SEA posted pro-regime messages and graphics, but the titles of the pages remained intact. Seventeen pages were infiltrated as of June 23. One of the pro-revolution pages allegedly published the names of the regime informants in Damascus, and another page was dedicated to thank Turkey’s Prime Minister Recep Tayyip Erdogan for “standing with the Syrian people.”
Anti-regime postings continued to appear in these pages and the number of each page’s fans has dropped significantly after the infiltration.
The SEA posted to its YouTube channel a video clip showing how it “attacked” the Facebook pages and how it replaced their logos with its own. At the time of publication, we are not able to conclusively determine how the compromise was technically implemented.
Conclusion
The Syrian Electronic Army’s recent activities are noteworthy for two reasons. First, the SEA re-defaced websites that were already defaced by an Iranian entity two weeks earlier. It is possible that the SEA has been able to exploit the same security vulnerabilities that the Iranian entity had exploited to re-deface these websites. However, it is also possible — but we determine of low probability — that the two parties are working together and that the Iranian entity gave the Syrian group backdoor access to the affected websites. We do not have sufficient evidence to support either hypothesis at the time of writing.
Second, it is interesting that the SEA continues to deface websites that it describes as hostile and responsible for antagonistic content, when the websites are mostly online businesses or personal websites not related to Syrian politics or the politics of the region. The SEA may be seeking publicity by claiming political significance to otherwise non-political websites, and targeting these web sites because they are simply vulnerable opportunities.
On the other hand, the SEA’s actions, regardless of the target, raise questions about the legal responsibility and international consequences of activities that manipulate and disrupt online businesses and personal websites in foreign jurisdictions. Such questions are particularly noteworthy when the group has a public online presence on a national network, and with the apparent blessing of the country’s president, vows to continue to engage in computer network exploitation.
Update June 25, 2011:
The SEA has claimed responsibility for attacking the website of the French embassy in Damascus on June 24, 2011 and 10 Israeli websites on June 25, 2011.
Users that try to access the news page of the French embassy in Damascus (http://www.ambafrance-sy.org/spip.php?rubrique112), are redirected to http://th3pro.pro/fr/ and displayed a page with text in French and Arabic claiming the defacement attack was to protest the “negative stand of the French government on Syria” and its participation in the “conspiracy against Syria”. The message also states the attack was to protest the inaccurate report of French news channel France 24 concerning the resignation of the Syrian Ambassador to France. The defacement page includes photos of supposedly pro-regime demonstrations in Syria, and is signed by the two SEA affiliated handles SaQeR SyRia and The PR0.
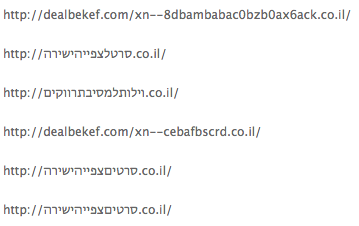
Figure 15: URLs defaced.
The defacement pages left on these sites read:
We Are the Syrian People , We Love our President Bashar Al Assad and we are going to return our Jolan Back , our Missiles will be landing on each one of you if you ever think of attacking our beloved land SYRIA
SaQeR.SyRia@Gmail.com
All of the affected websites are on the single IP 84.154.80.154 and hosted by a US-based server. None of these Israeli websites appear to contain political content.
The Information Warfare Monitor will continue to track and document SEA activities.
About the Information Warfare Monitor
The Information Warfare Monitor (IWM) is an advanced research activity tracking the emergence of cyberspace as a strategic domain. The IWM is public-private venture between two Canadian institutions: the Citizen Lab at the Munk School of Global Affairs, University of Toronto and The SecDev Group, an operational consultancy based in Ottawa, Canada.



